
Security, risk icon set

Digital security monochrome illustration

Collection of illustration icons of information processing

Cybercrime icon set

Security virus illustration set

Information processing illustration icon collection

Cyber Technology 01

Cyber crime

Ransom demanding fraudulent program

Cyber crime


Image of a cyber attack

Image of a warning against cyber attacks


Cyber crime

PC warning screen image


Cyber crime

Cyber crime

Cyber security

PC infected with ransomware virus

Hackers / crackers attacking other people's PCs


Cyber crime

PC malware virus detection warning screen

PC malware virus detection warning screen

Virus-infected smartphone

Virus-infected PC (desktop type)

Cyber crime

Net fraud icon

Smartphone junk mail

Virus-infected computer (notebook type, black)

Virus-infected smartphone

Virus-infected computer (notebook type, red)

cyber attack hospital

Virus-infected computer (notebook type, white)

Virus-infected PC (desktop type)

Virus that slips through security

Information processing illustration icon


Black hacker

Computer and virus mail icon

Tablet and impatient woman (suits)

Sumaho and an impatient woman (suit suits)

Smartphone trouble_virus

cyber attack

Virus-infected PC (desktop type)
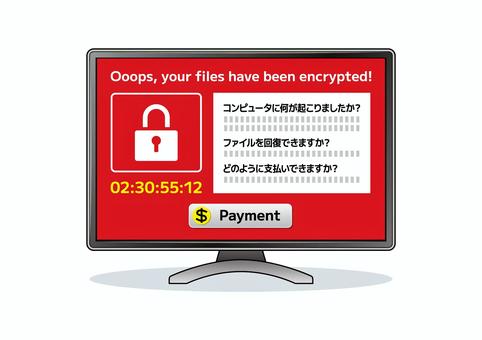
Computer screen infected with ransomware

laptop infected with ransomware

cyber attack hospital

cyber attack hospital

White hat hacker holding a shield

Image of a white hat hacker protecting a computer

Image of a white hat hacker protecting a computer

White hacker protecting a computer (line drawing)

cyber attack

cyber attack

cyber attack hospital

Cyber image "Hacker Threat" line drawing

Cyber attack image "hacker threat"

Dangerous communication with smartphones crayon illustration

Cyber attack image "attack" (line drawing)

Computer and spam flat icon

internet security icon

cyber attack

cyber attack hospital

cyber attack hospital

cyber attack hospital
68 Free vector clip art about .
Need vector clip art? Find the best free stock images about .
All the vector clip art is free even for commercial projects.

 © 2011 - 2025 ACworks Co.,Ltd. All rights reserved.
© 2011 - 2025 ACworks Co.,Ltd. All rights reserved.



